We’ve detected an increase in the number of domains containing the word facebook and which belong to malicious websites. What is clear is that cybercrooks are aware of the success of the social networks, especially Facebook, and consider them an entry point to distribute malware or to obtain credentials.
Among them there are the following:
facebook-ims.com
facebooks.bz
gjfacebook.com
image-facebook.com
ims-facebook.net
inbox-facebook.com
kfacebook.net
kjfacebook.net
lfacebooks.net
ojfacebook.net
ozfacebook.net
ppfacebooks.net
sodfacebook.com
ujfacebook.net
vfacebooks.net
vvfacebook.net
xfacebook.net
xxfacebooks.com
zfacebook.net
zxfacebook.net
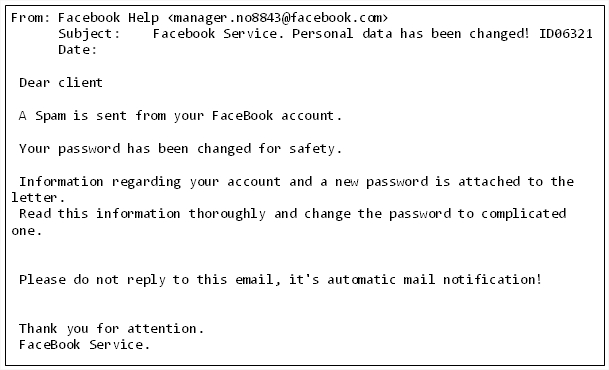
In most of the cases, when you access any of these URLs, a similar interface to real Facebook is displayed, in oder to obtain your access data. Then, you are redirected to the real site not to raise suspicion.
The following image is an example of the fake Facebook site. It may be easily identified not only because the content of the address bar doesn’t belong to the real Facebook but also because part of the text and the images are different:
This image belongs to the fake website:

As you can see, the web address does not belong to the original one:
![]()
This image belongs to the real website:

However, the purpose is not always to obtain user’s credentials, as from some of these websites malware is downloaded using the technique drive by download, in which the file is automatically run without user’s intervention.
We’ve seen that one of the samples that is being distributed through these websites is W32/Lolbot.C.worm.
Surely Facebook’s imitators will continue to appear, so when you access this or any other social network, don’t do it through links received via email, it’s better to type it directly in the address bar of the browser.



2 comments
Another good way to see it before it loads is to hover your mouse over the link and check the URL address that appears. If its not facebook.com or whatever dot com that you are familiar with DON’T CLICK ON IT EVER!! I am on number 56 of the “anti-virus 2010” FAKE viruses so far this year. And all the people who have it let the website first page open, and whammo, now fake popup windows all over the place, and over a very short time its gets way worse if you stay connected to the Internet.
Now you have to scrub and restore your Windows PC, or switch to Ubuntu/Linux or a Mac. Hope to be of help to you (since 1978). Truthfully yours, Bugs